What’s new in TensorFlow 2.4?
TF 2.4 is here! With increased support for distributed training and mixed precision, new NumPy frontend and tools for monitoring and diagnosing bottlenecks, this release is all about new features and enhancements for performance and scaling.
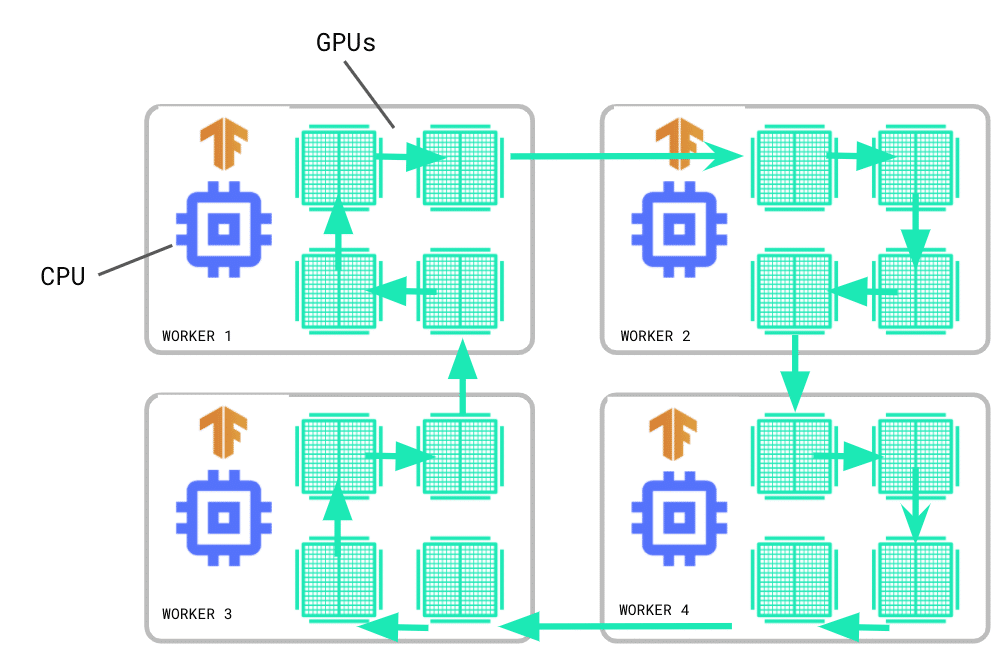
New Features in tf.distribute
Parameter Server Strategy
In 2.4, the tf.






