Cloud Security
GCP OAuth Token Hijacking in Google Cloud – Part 1
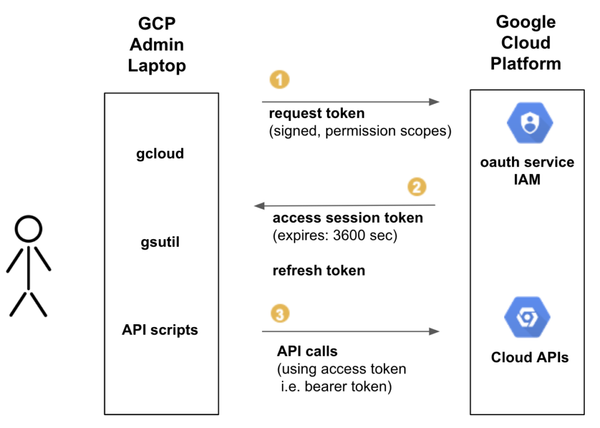
If an attacker compromises a Google Cloud Platform (GCP) user’s device, he can easily steal and abuse cached credentials, even if MFA is enabled. In this blog post, we will demonstrate an attack in real Google Cloud environments, involving: * Hijacking cached OAuth tokens stored on a GCP administrator’s