This is not a drill: VMware vuln with 9.8 severity rating is under attack
VMware is actively exploiting a vulnerability with a severity rating of 9.8 out of 10. At least one valid exploit has been made public, and successful efforts to hack servers running the vulnerable software have been made in the wild.
VMware product vulnerability gets a severity rating of 9.8 out of 10.
The vulnerability, identified as CVE-2021-21985, affects vCenter Server, a management tool for virtualization in big data centres. According to a VMware warning released last week, vCenter machines with default configurations include a problem that allows for the execution of malicious code on many networks when the machines are available through an open port.
Execution of code, without the need for authentication
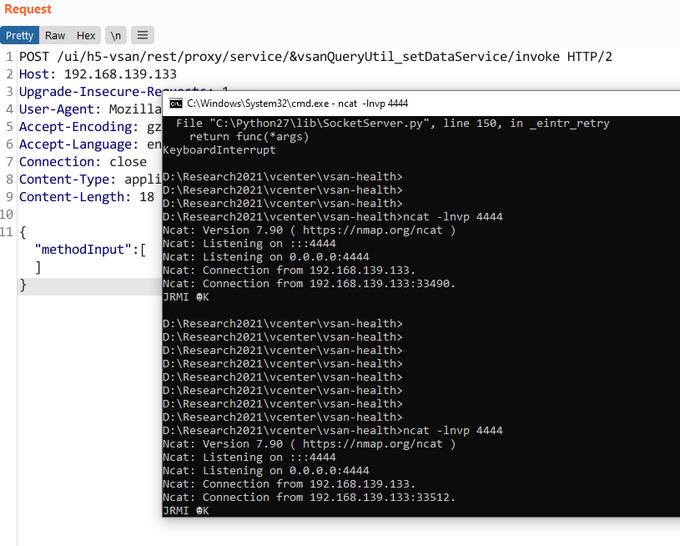
A researcher uploaded proof-of-concept code exploiting the weakness on Wednesday. According to a fellow researcher who requested anonymity, the exploit is reliable and requires minimal more work to utilise the code for nefarious purposes. It is possible to duplicate it by issuing five queries through cURL, a command-line programme for transferring data through HTTP, HTTPS, IMAP, and other commonly used Internet protocols.
Another researcher who tweeted about the disclosed exploit informed me he was able to alter it with a single mouse click to get remote code execution.
“Without any authentication method, it would obtain code execution on the target machine,” the researcher explained.
I own a web shell.
Meanwhile, researcher Kevin Beaumont said on Friday that one of his honeypots—a server linked to the Internet that runs out-of-date software in order for the researcher to watch active scanning and exploitation—began to notice scanning by distant systems looking for vulnerable servers.
He tweeted 35 minutes later, “Oh, one of my honeypots got popped with CVE-2021-21985 while I was working, I haz web shell (surprised it is not a coin miner).”
After successfully getting code execution on vulnerable machines, hackers employ a web shell as a command-line tool. Once installed, attackers from any location on the planet have nearly the same level of control as genuine administrators.
On Thursday, Troy Mursch of Bad Packets revealed that his honeypot had been receiving scans as well. On Friday, he added, the scans were continuing. The Cybersecurity and Infrastructure Security Administration issued an advisory shortly after this item was published.
It said as follows: “CISA is aware that cyber threat actors are likely to attempt to exploit CVE-2021-21985, a remote code execution vulnerability in VMware vCenter Server and VMware Cloud Foundation. Although updates were released on May 25, 2021, unpatched systems continue to be an attractive target, and attackers can exploit this vulnerability to gain control of an unpatched system.”
During a barrage
The in-the-wild behaviour is the latest source of frustration for administrators who have previously been subjected to a barrage of hostile exploits of other significant vulnerabilities. Since the start of the year, several applications used by major organisations have been targeted. In many cases, the vulnerabilities were zero-days, or exploits that were in use before to the release of a fix by the company.
Thousands of US organisations have been compromised in an ongoing Microsoft Exchange breach.
The attacks included successful exploits of Pulse Secure VPN vulnerabilities against federal agencies and defence contractors, the compromise of Sonicwall firewalls, the use of zero-day vulnerabilities in Microsoft Exchange to compromise tens of thousands of organisations in the United States, and the exploitation of organisations runni
As with the other abused products mentioned previously, vCenter is located in potentially vulnerable areas of major enterprises’ networks. Once attackers obtain control of the machines, it is frequently just a matter of time before they may migrate to areas of the network where espionage software or ransomware may be installed.
Administrators responsible for vCenter machines that have not yet been patched for CVE-2021-21985 should do so promptly. It would not be surprising to see an increase in attack volume by Monday.
